In 2017, more than 30,000 cell phones were searched at our borders — a 60 percent increase from 2016.
According to CBP, in fiscal year 2017, they searched and examined, 30,200 cellphones and other electronic devices, a nearly 60 percent increase from 2016.
While that’s a tiny percentage of the electronic devices brought into the U.S. by the more than 383 million international travelers arriving annually, it’s little comfort if your devices are the ones searched.
Everyone has personal information we want to keep private. Much of it is stored on our laptops, tablets and smartphones. Our contacts and calendar alone describe who we know and what we do each day. Business people often have confidential information and trade secrets on their electronic devices.
Once in the hands of CBP, we don’t know what will happen to our personal, private information, how it will be used, stored and how well it will be kept private. Unfortunately, we know that the government doesn’t have an enviable record in protecting its most confidential information. Too often it’s been hacked and leaked in recent years.
Until recently, data security primarily meant password- and passcode-based access and encryption security for our devices. Online information is generally secured through passwords, though today, two step authentication is sometimes available.
Biometric data security is now the norm
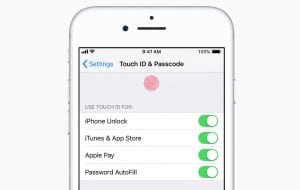
With the introduction of Touch ID by Apple in 2013, biometric fingerprint security quickly became an accepted security method, now used on many smartphones and tablets. Some smartphones use Facial ID security biometrics introduced by Apple in 2017. For the foreseeable future it appears as though biometric security will be the primary security methodology used for portable electronic devices, as it’s much faster and easier to use than passcodes.
LEARN IN TRAVELERS UNITED: 15 ways to prevent travel identity theft
Biometric-based security advances for electronic devices using the technology for logging into online accounts has occurred recently. Google rolled out support for the new FIDO 2.0 standard that Microsoft is also adopting. The new standard is the technology industry’s effort to move beyond password-based systems, which can be too easily hacked.
Most users aren’t aware of how easily hackers can break passwords, particularly passwords of eight characters or less.
According to Statista, in 2017, the last reported year, 50.5 percent of all leaked user passwords are eight characters long or less, which I think can be safely assumed is typical of all user passwords. When we test a strong password, meaning at least one capital letter, one small letter, one number and one symbol in an eight character password at How Secure Is My Password, we find that it would take a hacker just nine hours to crack the password.
READ ALSO: Your passport — 5 major myths exposed
If users bump their strong passwords by just two more characters to ten, it would take a hacker about 6 years to break it.
Of course, long passwords aren’t easy to remember, which is why so many users use the same password over and over again, or use well remembered information such as addresses, phone numbers, birth dates, family names, etc. That can dramatically help hackers crack a password or passcode quickly.
While passwords have definite problems, biometrics aren’t foolproof either. Researchers have reported successful hacks of fingerprint scanning and there have been reported hacks of Facial ID-based security.
At the U.S. border, however, another problem with biometric-based data exists.
Under U.S. law, the Fifth Amendment gives individuals the right to refuse to tell law enforcement something that might incriminate themselves. That includes not revealing an alphanumeric password or passcode that protects information on their electronic devices.
Fifth Amendment protection doesn’t cover biometric data security.
For example, criminal suspects are compelled to provide their fingerprints daily. At the border, CBP can compel visitors and citizens alike to unlock their electronic devices with their fingerprint. While there are no major court decisions concerning the use of Facial ID technology to unlock a smartphone, many legal experts expect the courts will treat Facial ID the same way as fingerprint-based security.
Here are three steps that travelers should take to protect their personal data on their electronic devices.
• Disable biometric data security. Biometric security provides no security for your personal data at the U.S. border, since CBP can compel you to use it to unlock your devices for their examination. Therefore, before entering the U.S., disable biometric security on your devices. You can enable it later, if desired.
• Use strong, long passwords and passcodes to protect your devices. Remember that while you can’t be compelled to reveal them, your devices can be seized to give CBP time to access and examine them if they are able. Visitors to the U.S. can be refused entry into the U.S. if they refuse CBP access to their devices.
• Remove as much personal data from your devices as possible after backing it up, prior to leaving on your journey. If you need to access it while traveling, store your data in the cloud for online access as needed.
Be careful and smart about your personal information and its access at the U.S. border. It can affect you, plus your family, friends and contacts listed and described in the data.
After many years working in corporate America as a chemical engineer, executive and eventually CFO of a multinational manufacturer, Ned founded a tech consulting company and later restarted NSL Photography, his photography business. Before entering the corporate world, Ned worked as a Public Health Engineer for the Philadelphia Department of Public Health. As a well known corporate, travel and wildlife photographer, Ned travels the world writing about travel and photography, as well as running photography workshops, seminars and photowalks. Visit Ned’s Photography Blog and Galleries.



